In our previous post, Post-Quantum Cryptography: A Critical Transition for Businesses, we discussed the steps organizations need to take to ensure a successful migration to post-quantum cryptography (PQC). In this post, we will focus on one of the key prerequisites: Identifying available PQC implementations and building a comprehensive inventory of cryptographic assets.
Why Is Inventory of Cryptographic Assets Important?
Building an inventory of cryptographic assets is a fundamental first step in the migration to quantum-safe systems and applications. Cryptographic assets are often deeply embedded within the various components that make up systems, applications, and infrastructure. Without a clear understanding of these assets, it is impossible to assess their risk and plan for mitigation.
In today’s agile, dynamic environments, businesses must stay ahead by thoroughly discovering and managing cryptographic assets. This ensures that organizations are prepared for the risks quantum computing poses to classical encryption techniques.
What Should an Inventory of Cryptographic Assets Contain?
A thorough cryptographic asset inventory needs to include:
- Cryptographic Keys: These are the fundamental building blocks used for encryption and decryption. For each key, details such as storage type, ownership, algorithm identifier, format, and status (active or deprecated) should be documented.
- Certificates: Certificates serve as electronic identities, often tied to public keys used in encryption. Information such as validity period, ownership, and algorithm used should be captured.
- Algorithms: Different cryptographic algorithms serve various functions, such as data encryption, authentication, and digital signatures. It is important to track which algorithms are in use, especially to identify algorithms that are vulnerable to quantum attacks.
- Protocols: Protocols such as TLS or IPSec specify how cryptographic operations should be carried out between two or more entities. Protocol version and implementation details should be part of the inventory to track any dependencies.
The Process of Building a Cryptographic Asset Inventory
Step 1: Discovery and Identification
The first step in building an inventory involves identifying where cryptographic assets are used across your infrastructure. These assets could be stored in:
- Certification Authorities (CAs)
- Servers and Databases
- Hardware Security Modules (HSMs)
- Network traffic, including encrypted traffic
- Cloud providers
- Containers and microservices
Given the complex and hybrid nature of modern IT environments, relying on manual methods like spreadsheets is impractical. Instead, automated tools and software solutions that support discovery across diverse platforms are essential.
Step 2: Collecting Asset Properties
Once discovered, you need to gather metadata about these cryptographic assets. This includes:
- Ownership: Who is responsible for managing the cryptographic asset?
- Application: What applications or systems are using the asset?
- Dependencies: What other systems, libraries, or services depend on the asset?
Understanding these details ensures that organizations have the necessary context to manage risks, particularly as they transition to post-quantum cryptography.
Step 3: Building a Robust Inventory
A well-structured inventory provides several benefits:
- Planning: It helps identify outdated algorithms and cryptographic assets that need to be replaced or upgraded.
- Risk Assessment: Regular monitoring of assets over time allows for proactive risk management, ensuring compliance and tracking progress toward quantum readiness.
- Identifying Dependencies: Knowing how cryptographic assets are interconnected can prevent system outages during the migration to PQC.
Leveraging the Cryptography Bill of Materials (CBOM)
To streamline and standardize the inventory process, many organizations are turning to the Cryptography Bill of Materials (CBOM). The CBOM is an extensible model that allows organizations to describe cryptographic assets and their dependencies in a structured format. It is part of the OWASP CycloneDX framework, which is designed to reduce cyber risks by providing a detailed picture of cryptographic infrastructure.
Key Features of CBOM
- Modeling Cryptographic Assets: CBOM provides a framework to model cryptographic assets, including keys, certificates, algorithms, and protocols.
- Capturing Asset Properties: It captures key attributes such as algorithm type, key length, usage details, and more.
- Tracking Dependencies: CBOM maps out dependencies between different cryptographic assets and the systems that use them.
- Compatibility with CycloneDX: The CBOM is fully compatible with the CycloneDX Software Bill of Materials (SBOM) standard, making it easier to integrate into existing supply chain management tools.
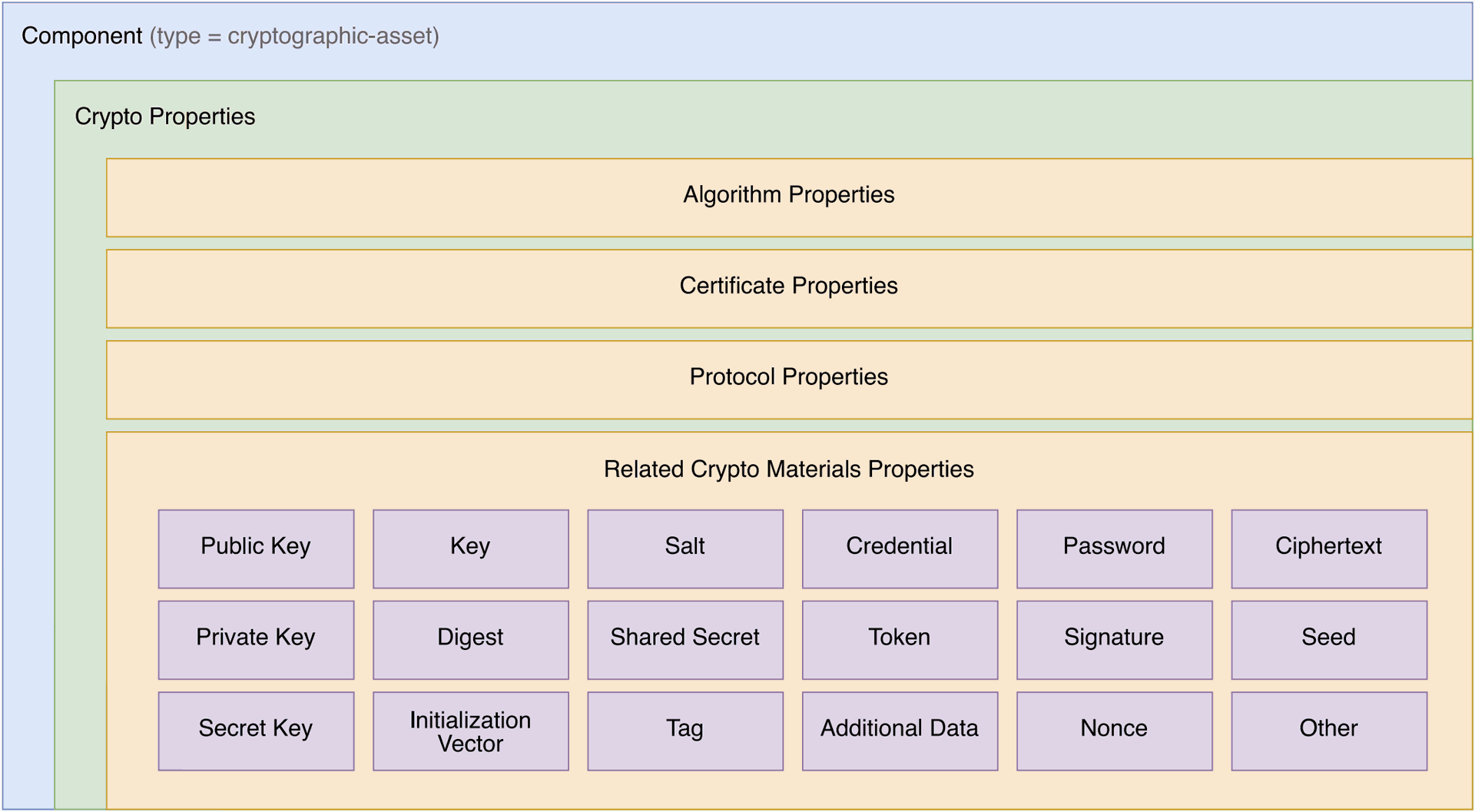
Example of CBOM
Here is an example of how a cryptographic key might be represented using CBOM:
Limitations of CBOM
While CBOM provides a structured, standardized approach to cataloging cryptographic assets, it does have some limitations. CBOM captures only static information—a snapshot of the current cryptographic environment. It does not dynamically update in real time, so it’s important to regularly refresh the inventory to account for changes in the environment.
Tools to Build a Cryptographic Inventory with CBOM
To help organizations adopt CBOM, several tools are available:
Provides an overview of the CBOM standard and includes a list of available tools. | |
A toolset designed to work with CBOM, offering features for cryptographic asset detection and management. | |
This plugin for SonarQube detects cryptographic assets in source code and generates CBOMs. | |
A tool for detecting cryptographic assets in container images and directories generating CBOMs. | |
This tool parses the output from CodeQL for cryptographic asset analysis and generates CBOMs. | |
A tool that analyzes over-the-wire TLS cryptography and generates CBOMs. |
Conclusion
Building a comprehensive cryptographic asset inventory is a vital step in migrating to post-quantum cryptography. As quantum computing continues to evolve, the need for organizations to protect their cryptographic infrastructure becomes more urgent. Tools like CBOM provide a structured and standardized approach to managing cryptographic assets, ensuring organizations are prepared for the quantum future.
By taking the time now to identify, document, and assess cryptographic assets, businesses can significantly reduce the risks associated with cryptography in the post-quantum era.
