On August 13th, 2024, the US National Institute of Standards and Technology (NIST) released new standards for three post-quantum cryptography (PQC) algorithms:
- FIPS 203 Module-Lattice-Based Key-Encapsulation Mechanism Standard, based on the CRYSTALS-Kyber algorithm
- FIPS 204 Module-Lattice-Based Digital Signature Standard, based on CRYSTALS-Dilithium algorithm
- FIPS 205 Stateless Hash-Based Digital Signature Standard, based on SPHINCS+ algorithm
These standards complement the earlier NIST SP 800-208 recommendation from October 2020, which covered stateful hash-based signature schemes, including the Leighton-Micali Signature (LMS) system and the eXtended Merkle Signature Scheme (XMSS).
This development marks a significant milestone for companies aiming to future-proof their cryptographic systems against the imminent threat of quantum-powered attacks. Organizations that have yet to begin their transition to PQC need to act now.
The Quantum Threat: Urgency for High-Risk Sectors
Quantum computing poses a substantial threat to classical encryption methods. McKinsey advises risk managers to focus on two key factors when preparing for quantum mitigation:
- Data Shelf Life: How long sensitive data must remain secure.
- System Life and Development Cycles: The timeline of system updates and improvements.
Industries such as finance, insurance, and government face particularly urgent challenges. These sectors manage cryptographic assets with long-term lifecycles, and any delay in implementing PQC could result in the compromise of highly sensitive data once quantum computing becomes mainstream.
Preparing for the Migration to Post-Quantum Cryptography
The migration to quantum-resistant cryptographic measures is complex, requiring a tailored approach for each organization. While there's no universal solution, several key resources provide critical insights for businesses planning their transition:
- NIST Migration to Post-Quantum Cryptography - NCCoE
- ENISA Post-Quantum Cryptography - Integration study
- ANSSI VIEWS ON THE POST-QUANTUM CRYPTOGRAPHY TRANSITION
- TR 103 619 - Migration strategies and recommendations to Quantum Safe schemes
- PMMP PQC Migration Management Process
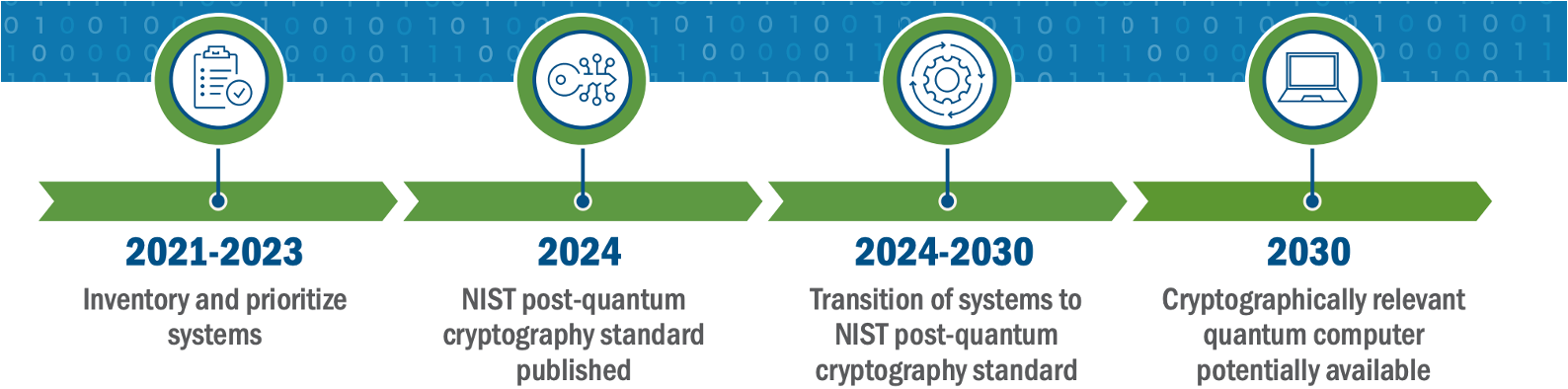
U.S. Department of Homeland Security transition infographics.
These resources, along with infographics from the U.S. Department of Homeland Security, outline various strategies. However, there’s no consensus on whether organizations should begin with hybrid solutions (combining classical and quantum-resistant algorithms) or move fully to post-quantum algorithms. Regardless, all plans share common steps.
Building organizational awareness is the foundation of any successful migration. Employees must understand the quantum threat and its potential impact on the organization. This education should encompass:
- Training and workshops on quantum computing and cryptography
- Discussions with senior management to align on priorities and secure resources
- Guidance and demonstrations to help technical teams grasp the migration process
Without adequate understanding, organizations risk under-allocating resources and delaying essential security updates.
Organizations must assess the current state of post-quantum cryptographic technologies and evaluate their readiness. This includes:
- Identifying available PQC implementations
- Discussing preparedness with technology vendors
- Testing quantum-resistant solutions in existing systems
A detailed inventory of cryptographic assets (keys, protocols, and usage) is critical for evaluating the current infrastructure and prioritizing systems for migration. A complete asset inventory informs strategic decisions and helps avoid gaps in security during the transition.
Cryptographic agility refers to the ability to swiftly switch between cryptographic algorithms without major disruptions. As the landscape of cryptography continues to evolve, agility becomes a necessity for systems relying on encryption. Implementing cryptographic agility allows organizations to respond dynamically to new threats, including those posed by quantum computing.
Before beginning the migration, organizations must conduct a thorough risk assessment. This assessment informs decisions on which systems to migrate first and helps prioritize migration efforts based on criticality and exposure to quantum threats.
Effective migration requires project management, with defined timelines, costs, and communication channels. Collaboration with stakeholders, vendors, and partners is essential to ensure a smooth transition and continuous security.
Challenges in the PQC Transition
Migrating to post-quantum cryptography comes with its own set of challenges:
- Coordination with external partners and third-party vendors
- Increased key size and computational resource demands
- Compatibility with legacy applications that rely on older cryptographic methods
- Securing already-encrypted data, which may be vulnerable to future quantum decryption
- Lack of precise data on cryptographic objects and their use
- Limited automation and crypto-agility tools to streamline the migration
- Insufficient investment in PQC technologies and awareness
Preparing for a Successful Migration
A successful PQC migration involves several key assumptions:
- Strong project sponsorship from senior leadership to ensure resources and attention
- Comprehensive use-case documentation to guide implementation
- Skilled personnel capable of managing cryptographic transitions
- Ranking of cryptographic use-cases based on their complexity and importance
- Thorough visibility and inventory of existing cryptographic systems
Having the right technology stack in place is essential for a seamless transition. Organizations need to ensure they are prepared with the necessary tools and frameworks for a successful migration.
How 3Key Can Help
At 3Key, we specialize in guiding organizations through the complexities of post-quantum cryptography projects. We offer consulting services to help companies:
- Understand the quantum threat and its implications
- Build an inventory of cryptographic assets
- Design and implement a future-proof cryptographic infrastructure
Our team analyzes the current state of your security infrastructure and collaborates with your organization to develop tailored solutions that align with your business goals. Let us help you prepare for the quantum future and safeguard your cryptographic assets.
